
The integral role of threat assessments
Security in your own system
Threat analyses play an integral role in MaibornWolff’s approach to cybersecurity. This enables customers to assess their own situation correctly and take measures efficiently. Until now, the documentation and maintenance effort of such an analysis posed a major challenge to our consultants. ThreatSea declares war on long threat lists in Excel and empowers development teams to seamlessly integrate the approach into agile cycles. Through our unique 4×6 methodology, precise suggestions are delivered along the way. They support the team to implement exactly the right level of security in their own system in a targeted and efficient way.

Develop comprehensive and clear concrete attack scenarios
The 4×6 methodology
Based on our long-standing experience, we have developed the so-called “4×6 methodology”. At its core, it is based on an abstraction of IT systems, the attacks possible on them, and potential attackers. From a technical perspective, IT systems are divided into six classes of attack points and attackers into four authorization levels. This results in a 4×6 matrix of possible attacks. This matrix – applied to a specific system architecture – provides the team with a direct, targeted entry point for discussion when recording and evaluating threats.

ThreatSea makes the practical use of all steps of the 4×6 method much more effective, from system modeling to the presentation of results. The goal is not only to save time, which can sometimes take days in large projects, but above all to focus on the content.
Johannes Geiger; Security architect at MaibornWolff and inventor of the 4×6 method

4 steps to a complete risk analysis
Core features
With ThreatSea and the 4×6 methodology, MaibornWolff offers its own approach to threat analysis that targets system experts. We are convinced that if they are properly empowered, they can make the best decisions for their own system.

1. Assessment of protection requirements
When determining the protection requirements, all information objects worthy of protection are systematically recorded. The protection goals of confidentiality, integrity and availability are assessed.

2. Structure analysis
The system image editor is the heart of ThreatSea. Here, the IT solution under investigation can be easily modeled graphically. The mapping of previously captured assets to individual elements enables ThreatSea to determine a component-specific protection requirement – and thus calculate exact impact assessments for concrete threat scenarios. Adjustments to the system image are applied directly to the threat list. Agile teams can thus continuously track system changes and their impact on the threat landscape.
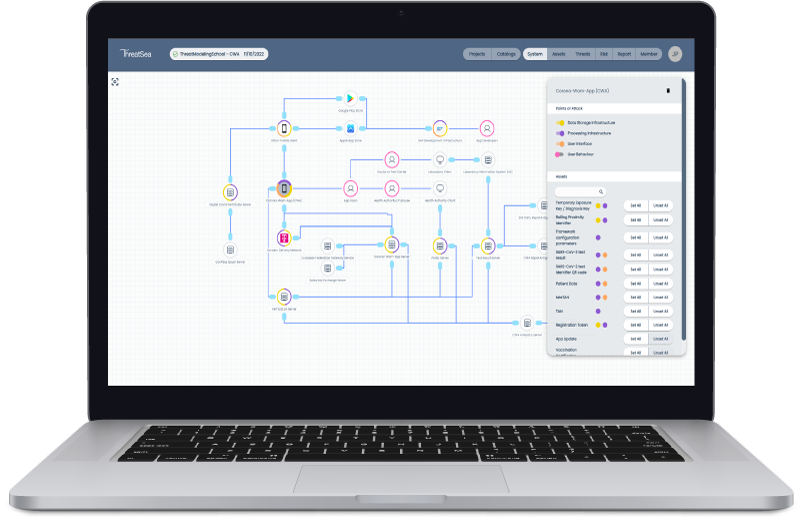
4. Recording measures
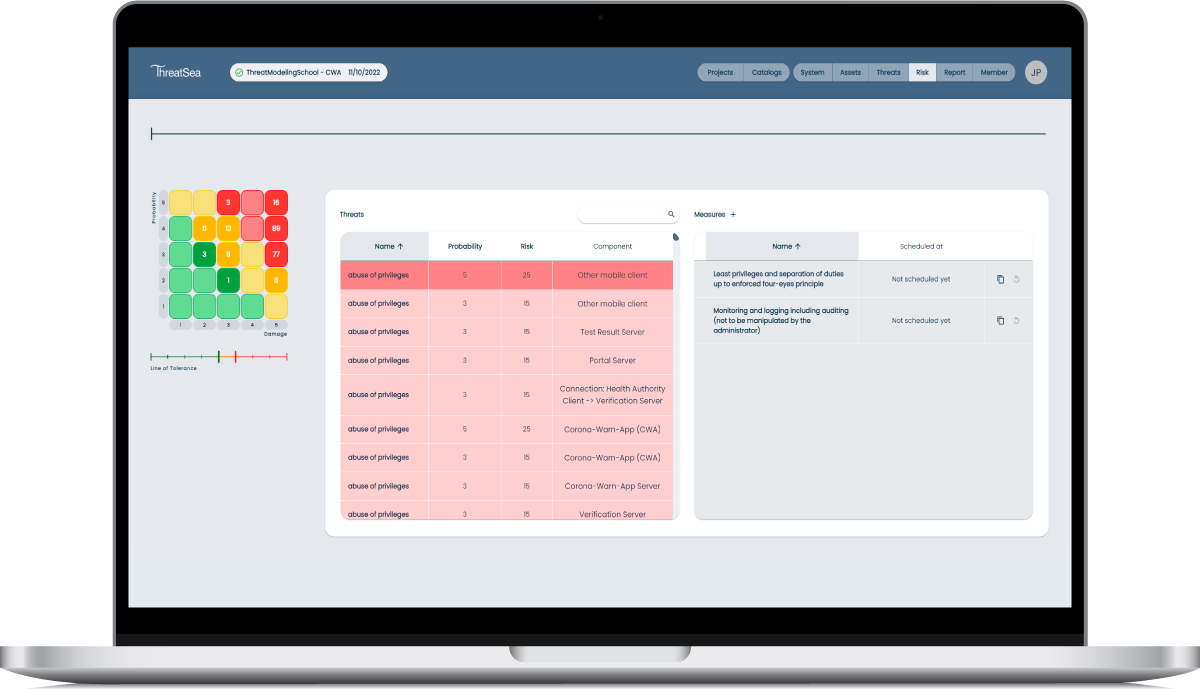
In addition to a complete risk analysis, ThreatSea directly illustrates the impact of security measures. Thanks to the 4×6 methodology, generic measures are also proposed, which can be specified and provided with a time schedule. With the help of the dynamic risk matrix, it can be clearly demonstrated how the measures gradually affect the risk profile.
A cooperation with the University of Mannheim
Origin of ThreatSea
When using the 4×6 method for the first time, we quickly realized: While the 4×6 method impresses with its simplicity, the documentation effort is quite high.
Therefore, we had our subject-specific requirements implemented by five highly motivated student teams in a software development project at the Mannheim University of Applied Sciences. The project enriched us not only with completely new perspectives on the usability of the methodology, but also with five fully functional prototypes.
The winning team’s ThreatSea prototype impressed with a unique user experience, feature richness, and additionally echoed the abstraction idea of the methodology.
Since then, the Cybersecurity department continues to work on ThreatSea and has brought the original prototype to production maturity. ThreatSea and the 4×6 methodology have proven themselves multiple times in customer deployments and are indispensable for us in threat and risk analyses.
Programming languages:
- Javascript
Frameworks | Tools | (Cloud-)Platforms
- React
- Redux
- Azure
- Kubernetes
- Docker
- Gitlab CI/CD
Learn more

